The digital landscape of 2026 presents unprecedented cybersecurity challenges. As businesses increasingly adopt cloud infrastructure, integrate AI tools, and manage distributed workforces, the attack surface has expanded dramatically. According to recent reports, cyberattacks have become more sophisticated, with hackers exploiting vulnerabilities across multiple touchpoints simultaneously.
For businesses navigating this complex environment, understanding how to protect sensitive data isn’t optional. Let’s explore the critical security strategies every organization needs to implement today.
The New Threat Landscape
The convergence of cloud computing, artificial intelligence, and remote work has created a perfect storm for cybercriminals. Traditional perimeter-based security models no longer suffice when employees access corporate resources from home offices, coffee shops, and co-working spaces using various devices.
AI-powered attacks are becoming more prevalent, with hackers using machine learning to identify patterns in security systems and exploit weaknesses faster than human analysts can detect them. Meanwhile, cloud misconfigurations remain one of the leading causes of data breaches, often resulting from rapid deployment without proper security protocols.
Remote work has introduced additional complications. When employees connect through unsecured home networks or public Wi-Fi, they create entry points that bypass traditional corporate firewalls. The shift to distributed teams means sensitive data now travels across countless networks before reaching its destination.
Cloud Security: Your First Line of Defense
Securing cloud infrastructure requires a multi-layered approach. Start by implementing zero-trust architecture, which assumes no user or device should be trusted by default, regardless of whether they’re inside or outside the network perimeter. Every access request must be verified, authenticated, and continuously validated.
Cloud security solutions should include encryption both in transit and at rest. This ensures that even if data is intercepted, it remains unreadable without proper decryption keys. Regular security audits and penetration testing help identify vulnerabilities before attackers can exploit them.
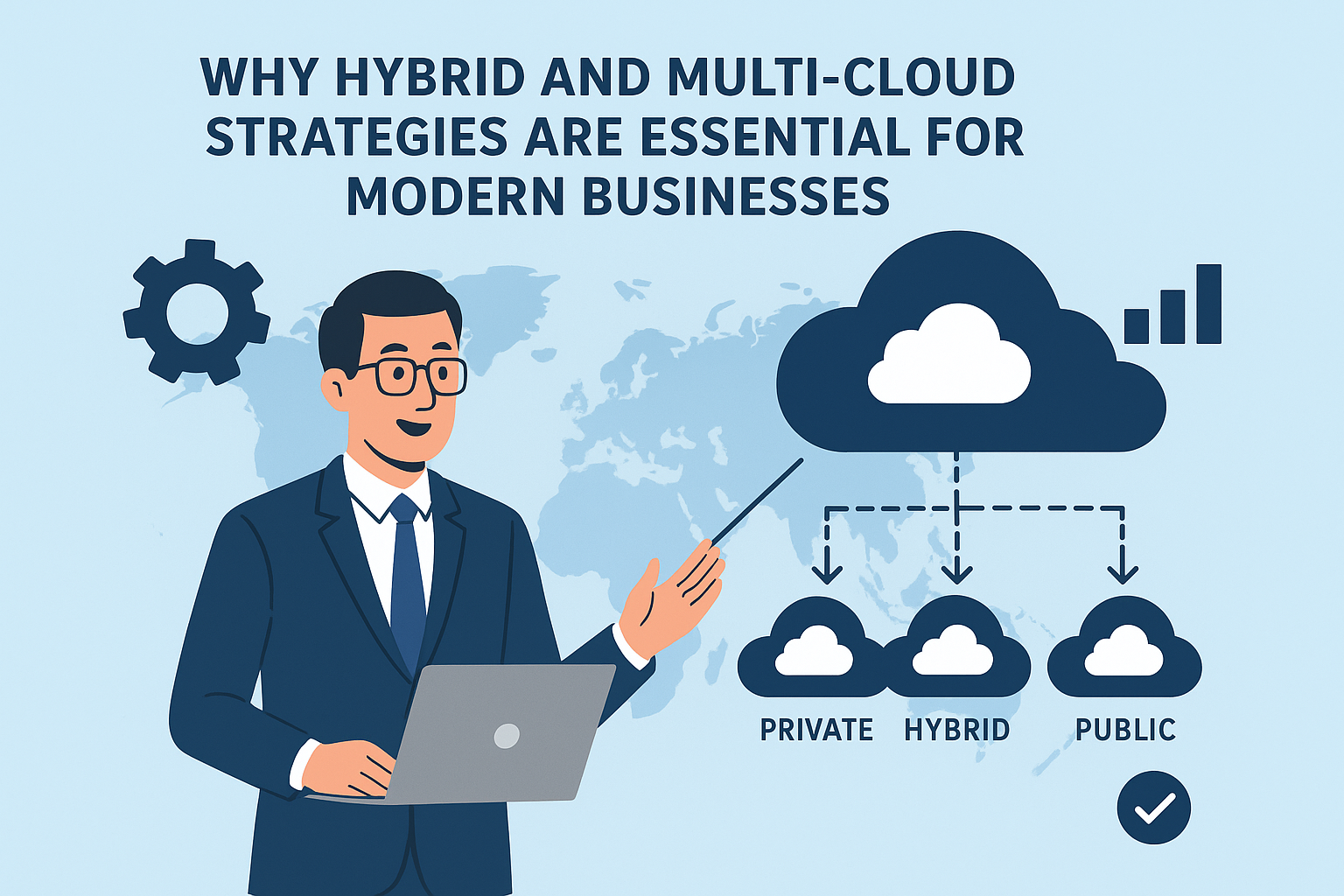
For businesses leveraging hybrid and multi-cloud strategies, maintaining consistent security policies across different platforms is crucial. Each cloud provider has unique security features and responsibilities, and understanding the shared responsibility model prevents dangerous gaps in protection.
AI Security: Protecting Your Most Valuable Assets
As businesses integrate AI tools into operations, they must consider both the security of AI systems themselves and how AI can enhance overall cybersecurity posture. AI models trained on sensitive data can become targets, with adversaries attempting to extract proprietary information through model inversion attacks.
Implement robust access controls around AI systems and regularly audit who can access training data and model parameters. Consider using federated learning approaches that allow AI models to learn from distributed datasets without centralizing sensitive information.
On the defensive side, AI-powered security tools can analyze network traffic patterns, detect anomalies in real-time, and respond to threats faster than traditional methods. Machine learning algorithms can identify unusual user behavior that might indicate compromised credentials, even when the login appears legitimate.
Securing Remote Work Environments
Remote work infrastructure demands specific security measures. Virtual Private Networks (VPNs) encrypt connections between remote devices and corporate networks, but they’re not foolproof. Implement multi-factor authentication (MFA) across all systems, passwords alone provide insufficient protection in 2026.
Endpoint security becomes critical when devices are scattered across locations. Deploy endpoint detection and response (EDR) tools that monitor device activity, detect suspicious behavior, and can isolate compromised endpoints before threats spread across the network.
Regular employee security training is equally important. Human error remains the weakest link in cybersecurity. Teach teams to recognize phishing attempts, practice good password hygiene, and understand the consequences of security breaches. Monthly refresher training keeps security awareness top of mind.
The Importance of Data Backup and Disaster Recovery
Even with robust security measures, breaches can occur. Having a comprehensive disaster recovery and business continuity plan ensures business operations continue even after a security incident.
Implement the 3-2-1 backup rule: maintain three copies of data on two different media types, with one copy stored offsite. Regular backup testing verifies that data can actually be restored when needed, many organizations discover their backups are corrupted only during a crisis.
Staying Compliant and Vigilant
Data security compliance with regulations like GDPR, HIPAA, and industry-specific standards isn’t just about avoiding fines. These frameworks provide structured approaches to protecting customer data and maintaining trust.
Regular security assessments, vulnerability scanning, and threat intelligence monitoring help organizations stay ahead of emerging threats. Cybersecurity isn’t a one-time project but an ongoing process that evolves with the threat landscape.
Conclusion
Protecting business data in 2026 requires a holistic approach that addresses cloud security, AI vulnerabilities, and remote work challenges simultaneously. By implementing zero-trust principles, leveraging AI-powered security tools, securing endpoints, and maintaining robust backup systems, businesses can significantly reduce their risk exposure.
The cost of prevention is always lower than the cost of recovery. Investing in comprehensive cybersecurity measures today protects not just data, but your organization’s reputation, customer trust, and long-term viability. Contact us to learn how Informatics360 can help secure your digital infrastructure.